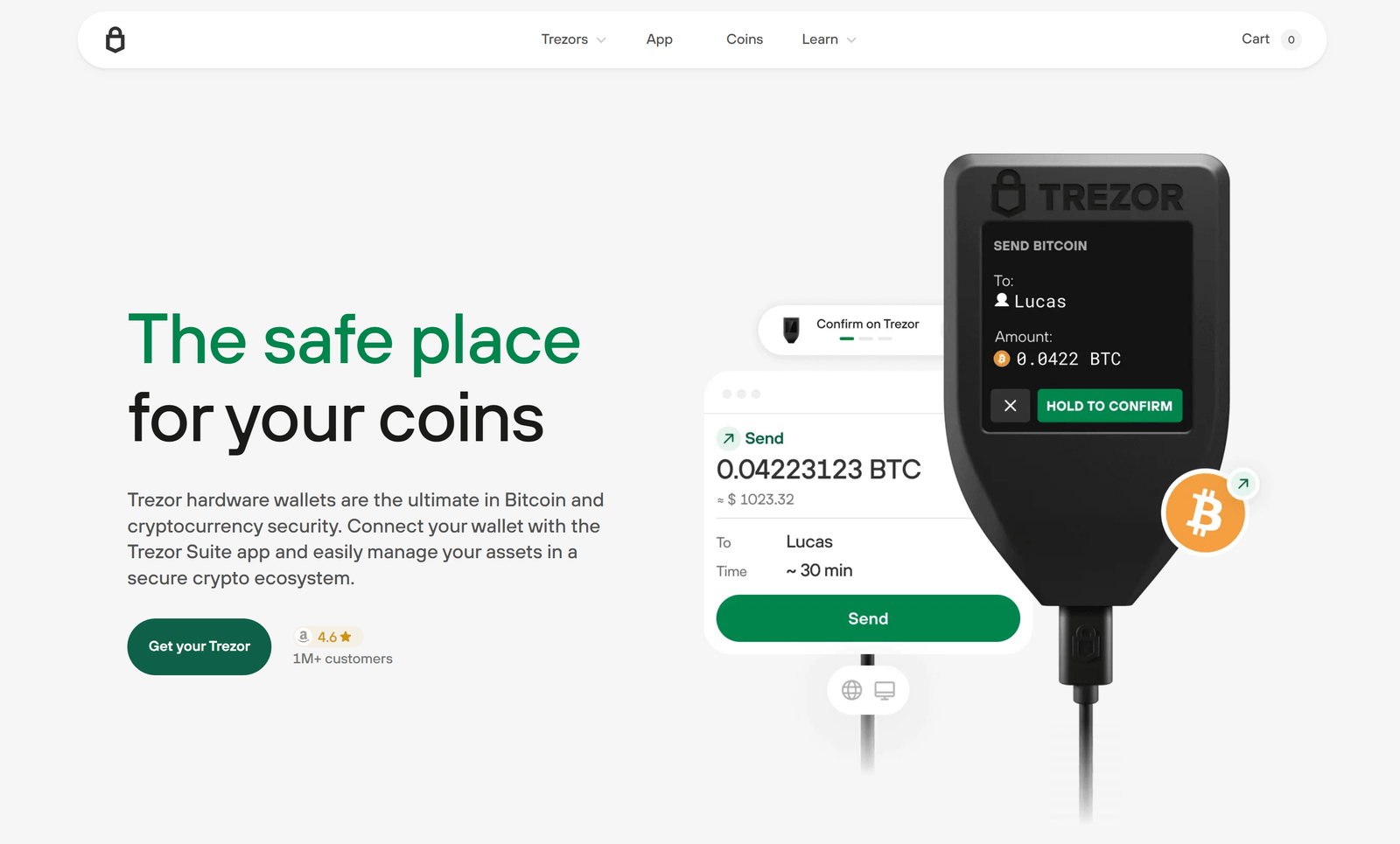
Trezor.io/Start is the secure starting point for anyone ready to take full control of their digital assets. Trezor, the pioneer of hardware wallets, allows users to store private keys offline—completely safe from hackers and phishing attacks. The setup wizard at Trezor.io/Start guides you step by step, ensuring your wallet is initialized safely, verified properly, and ready for everyday crypto use.
In an era of constant digital threats, self-custody has never been more important. Trezor empowers you to hold your wealth independently. No middlemen, no cloud risks—just pure, local encryption sealed by the power of hardware security.
Getting started at Trezor.io/Start is simple but deeply secure. Follow these core phases:
Each stage is designed to eliminate user error. The interface educates you as you go, explaining exactly why each security action matters.
Trezor isn’t merely a gadget—it’s a philosophy of digital independence. Born from the vision of open-source freedom, it teaches users to protect their crypto not by trusting companies, but by understanding technology. Every line of firmware, every circuit, every UI element is open for community audit. That’s why security experts worldwide trust Trezor.
When you start at Trezor.io/Start, you aren’t just setting up a wallet—you’re joining a movement for self-sovereignty in the digital age.
Every Trezor feature is built with one rule: security first. Convenience is added only when it strengthens user protection.
When initializing your wallet, your device randomly generates a recovery seed phrase. This 12- or 24-word sequence is the cryptographic root of all your coins. It is displayed only once—offline—and must be written on paper or metal backup sheets. Losing it means losing access forever; exposing it means losing funds to anyone who copies it.
Once written down, your Trezor locks that seed inside its chip. It never transfers it to your computer or the internet. That’s the heart of Trezor’s design: even a compromised computer can’t extract your private keys.
The Trezor Suite App extends the power of your hardware wallet into a clean, encrypted dashboard. Here, you can monitor your balances, exchange assets, view price charts, and connect to decentralized apps—all while keeping signing isolated on your hardware device.
With built-in Tor integration, privacy mode, and multiple account management, Trezor Suite turns your desktop into a secure crypto cockpit.
Phishing websites often attempt to imitate Trezor to steal recovery seeds. The real Trezor.io/Start uses HTTPS encryption and will never request your seed or private keys online. Always check the URL bar—if it doesn’t say “trezor.io,” close it immediately.
The official setup page also provides firmware updates signed by Trezor’s cryptographic keys. This guarantees that your device runs authentic code verified by the manufacturer.
Follow these rules and your crypto becomes virtually unhackable. Remember, the strength of hardware wallets lies not just in technology but in disciplined use.
As the digital economy evolves, centralized exchanges face scrutiny and breaches. More investors are choosing hardware wallets as the gold standard of crypto security. Trezor leads this movement by combining usability, transparency, and education.
Starting at Trezor.io/Start today means securing tomorrow’s digital freedom. Each Trezor user strengthens the decentralized ethos that keeps crypto independent from traditional finance.
Unbox your Trezor, connect it, visit Trezor.io/Start, and let the secure setup begin. Within minutes, you’ll have a personal vault capable of safeguarding Bitcoin, Ethereum, NFTs, and tokens—all without surrendering control to anyone else.